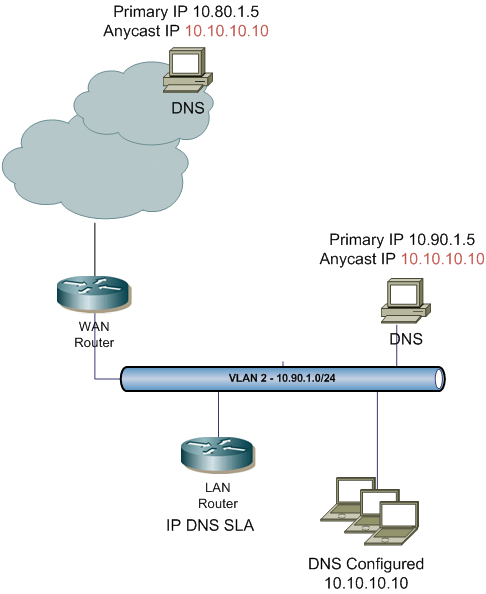
Recently I came across an idea to implement anycast DNS within an enterprise environment. The concept is similar to Google’s public DNS, but at an enterprise level. Using IP SLA DNS, a static tracked route and some redistribution it makes it an easy solution. The biggest benefits is that all internal clients can use the same DNS IP address no matter what locations they reside in; additional benefit is distributing the load when DNS attacks occur.
First you’ll have to configure the Cisco’s IP SLA. Using the DNS feature is much better than just ICMP. It will actually verify that the DNS server is responding to a specified query. In my example below I’m using a query for test001dns.me which is configured on the server as an A record. The DNS query is sent to a distinct IP address of the server 10.90.1.5. All local DNS server have two IP addresses: distinct and anycast. The anycast address is configured as a secondary IP (10.10.10.10) a numerous DNS servers throughout the enterprise.
Below is the IP SLA configuration using the DNS feature. It is configured on a LAN router.
ip sla 10 dns test001dns.me name-server 10.90.1.5 timeout 15000 owner Anycast-DNS ip sla schedule 10 life forever start-time now
Create a tracked object to use the IP SLA, for a static route in the next set.
track 1 ip sla 10
This is where it get’s little tricky within the static route. The static host route points to the anycast IP address configured on the DNS server. It points to an interface of the network 10.90.1.0/24, the vlan that the DNS is on. I’m applying the track 1 option to install this route only when ip sla 10 is operational..i.e. it responds to the query for test001dns.me. This route is tagged with a value 888. It will be used to redistribute locally. As a future reference, I’m naming it DNS-ANYCAST to know what that route is used for.
ip route 10.10.10.10 255.255.255.255 Vlan2 tag 888 name DNS-ANYCAST track 1
That static anycast route is redistributed using a route-map which matches any statics tagged with 888. It is redistributed as a OSPF external type 2 route, with metric 10. Any other advertisements of this anycast host route should have a much higher metric. These should come from other locations or datacenters hosing the anycast DNS servers. The other locations should have a similar configuration.
router ospf 1 redistribute static metric 10 metric-type 2 subnets tag 888 route-map STATIC-INTO-OSPF
route-map STATIC-INTO-OSPF permit 10 description DNS ANYCAST match tag 888
For security reasons you might want to block any access to the distinct IP of the DNS server (10.90.1.5) and only allow access from the router performing the IP DNS SLA.
This was an easy and simple configuration. The rest is dependent on your WAN, but you get the general idea how to do it at each location when you host these anycast DNS servers throughout the enterprise.